Injection Methods
- Self Injection
- The malware allocates regions of memory within its own memory space and unpacks (deobfuscates/decrypts) the payload there
- Remote Process Injection
- The malware spawns a new process and injects the payload in that memory region
Remote Process Injection Methods
DLL Injection
- Executes a malicious DLL inside a remote process
- A DLL is a shared library that process use to call existing functions
- By manipulating the order of loading of DLLs, the attacker can make a process load a DLL with malicious functions
APIs used
OpenProcess() VirtualAllocEx() WriteProcessMemory() LoadLibraryA() GetProcAddress() CreateRemoteThread() WaitForSingleObject()
Sample of how this works: the binary calls
CreateToolhelp32Snapshot which returns a list of running processesIn one of the process, it opens the process and calls
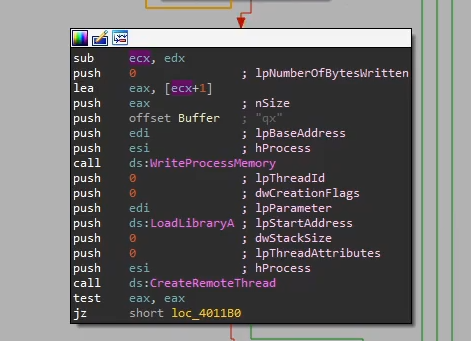
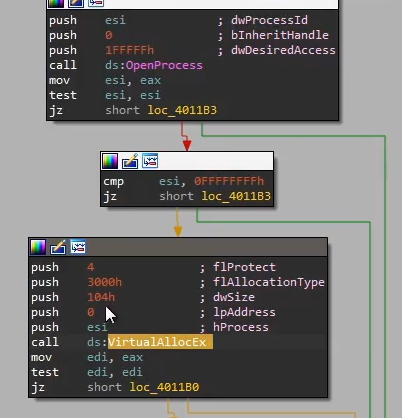
VirtualAllocEx to allocate a memory region within the process, and calls WriteProcessMemory and LoadLibraryA to load the malicious DLL. Finally it calls CreateRemoteThread to create a separate thread with the loaded malicious DLL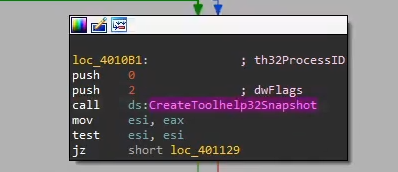
Reflected DLL
Injecting a DLL without ever touching the disk. This is different from the traditional DLL shown above where the malware has to write the malicious DLL to disk first before injecting it to a remote process.
PE Injection
- Executes a binary/shellcode inside a remote process
- Allocates memory within a legitimate process
- Writes the malicious code in the allocated memory
- Executes code by calling
CreateRemoteThread()
APIs used
OpenProcess() VirtualAllocEx() WriteProcessMemory() VirtualProtectEx() CreateRemoteThread() CreateProcessInternalW() WaitForSingleObject() NtWriteVirtualMemory() NtWriteVirtualMemory(ProcessHandle, DestBuffer, SrcBuffer, NumberOfBytesToWrite, NumberOfBytesWritten);
We see
CreateProcessInternalW() creating a process mstsc.exe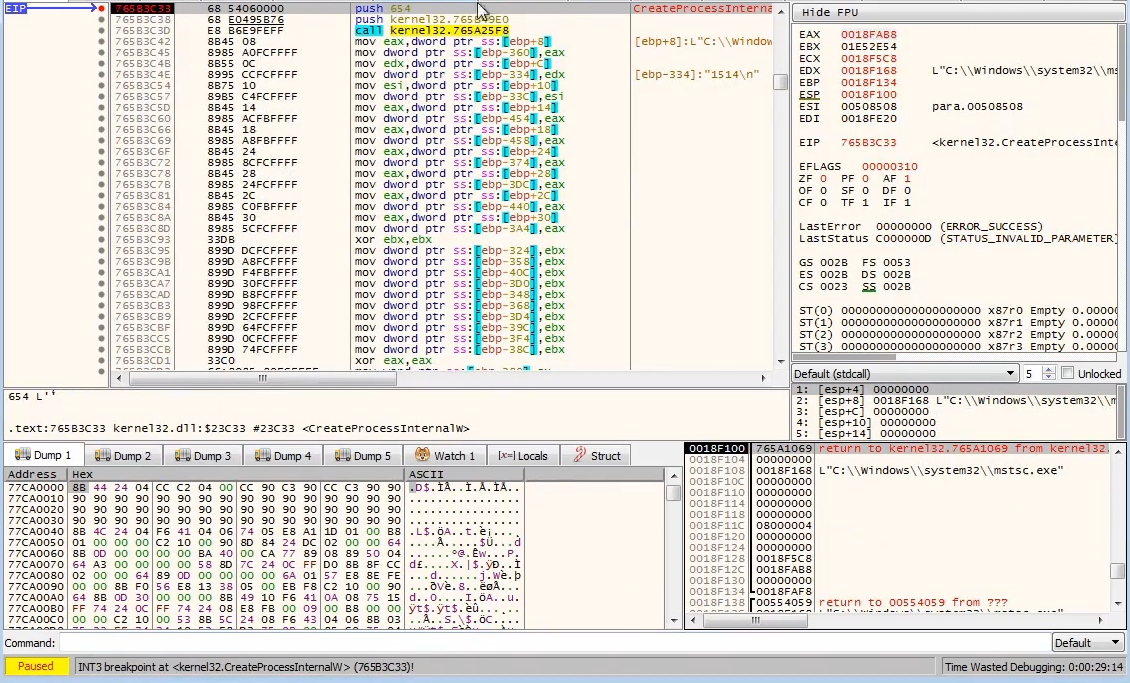
Then we see
NtWriteVirtualMemory(), but the size it’s writing is tiny, so it’s likely not the payload (0x20)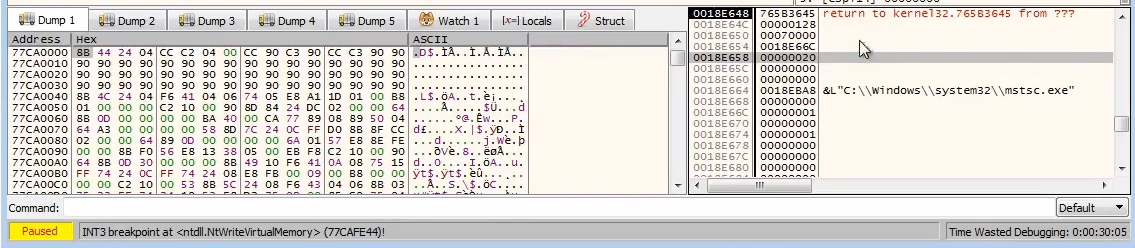
In another hit of
NtWriteVirtualMemory(), we see it writing a larger size payload, which is likely the injection to the process. It writing a payload of size 0x7924 to memory address 0x8006C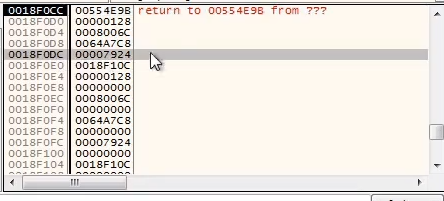
We follow dump in
0x64A7C8 to view the source of what it’s writing, and click Follow in Diassembler to view the instructions of the payload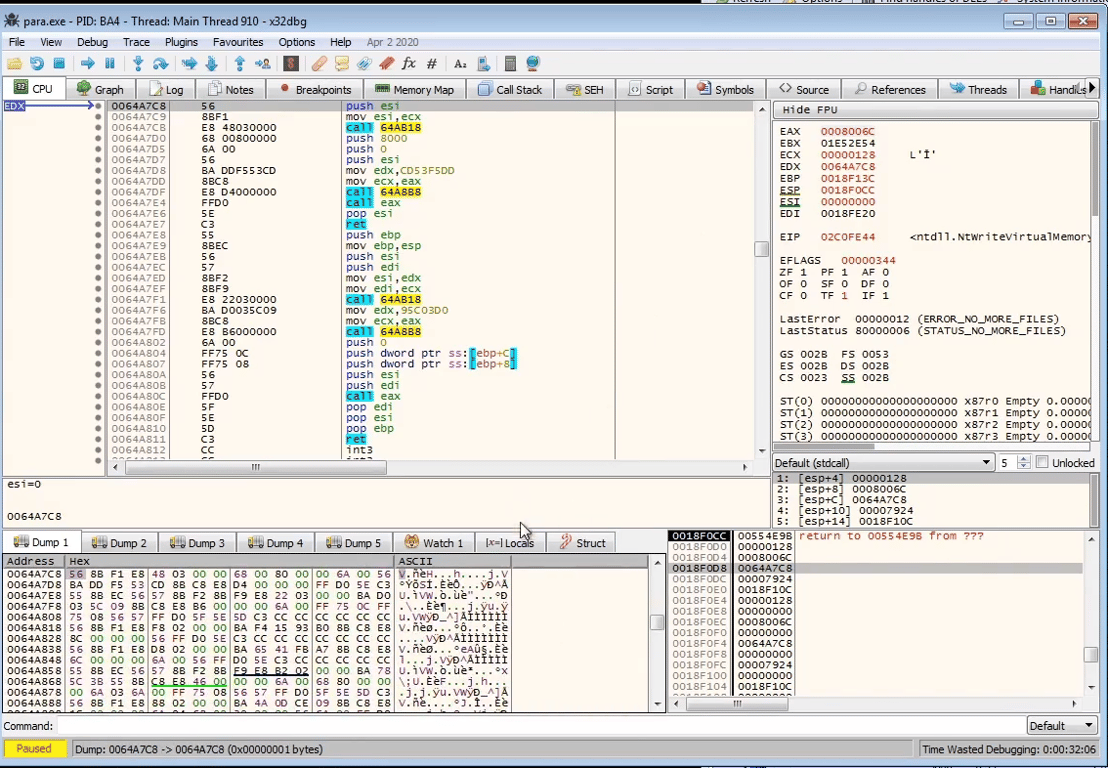
Look out for calls
NtWriteVirtualMemory calls that write a jmp instruction to the target binary. It could mean that it’s messing with the entry pointFollow DWORD in current dump and we see an E9 which is a jmp. It’s writing this code to address 0x388530.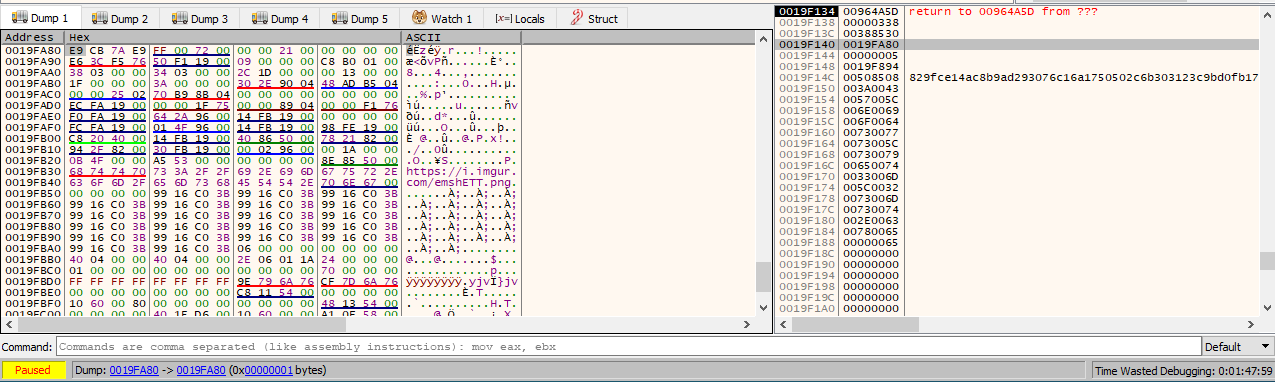

In the attached process, we attach to the newly spawned process and hit
ctrl-g to go to address 0x388530 and set a breakpoint thereAfter the parent process calls resume thread, we should break on the child processes “real” entry point
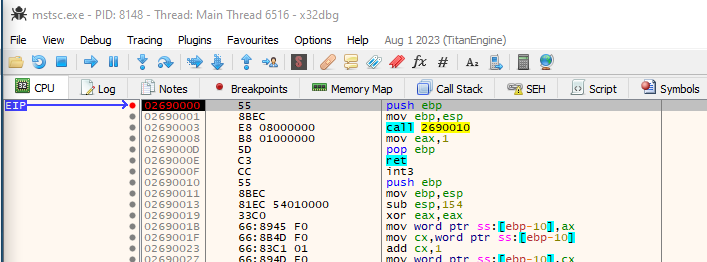
Process Hollowing
- Executes a process and then suspends it and overwrites the memory with malicious code and resumes
APIs used
CreateProcessA() # look for arguemnt to put it in a suspended state NtUnmapViewOfSection() VirtualAllocEx() ReadProcessMemory() WriteProcessMemory() VirtualProtectEx() GetThreadContext() SetThreadContext() ResumeThread()
The parameter
4 in CreateProcessA indicates that it’s creating a processes in a suspended state. This is an indicator of Process Hollowing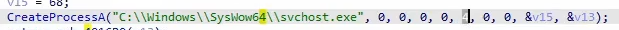
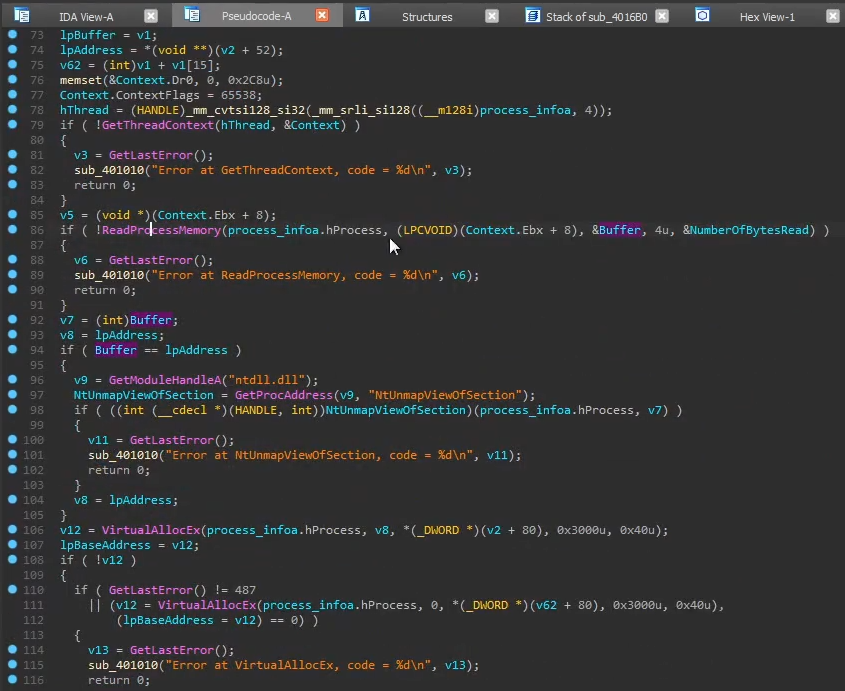
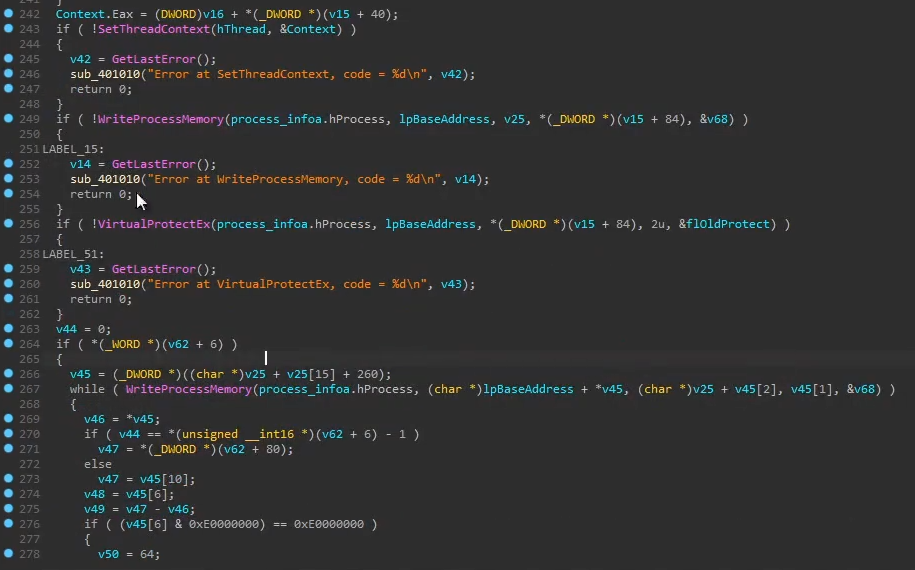
In the code below which does Process Hollowing:
- Gets the processes context by running
GetThreadContexton line 79
- Unmap whatever is in the process by calling
NtUnmapViewOfSectionon line 97
- Allocates a new region of memory within the process by calling
VirtualAllocExon line 106
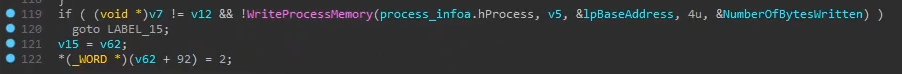
- Writes the payload into the allocated region of memory by calling
WriteProcessMemoryon line 119
- Set the new context of the thread by calling
SetThreadContexton line 243
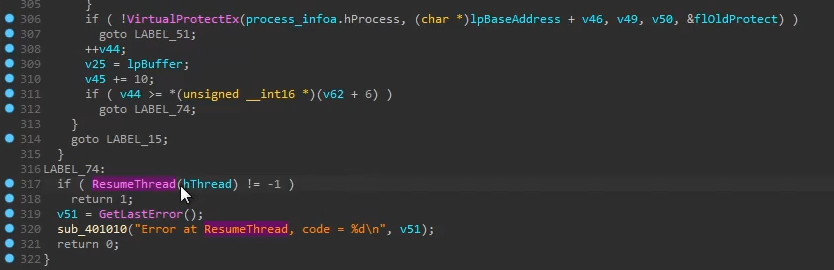
- Performs more writing of code to the allocated memory
- Changes the RWX permissions by calling
VirtualProtectExon line 306
- Resumes the thread by calling
ResumeThreadon line 317
Process Doppelganging
- Opens a target executable for writing (on disk)
- Overwrites the target executable with malicious content (on disk)
- A section is created using the overwritten target executable (in memory)
- The overwritten target executable is rolled back to its original state( on disk)
- The section in memory is executed (in memory)
APIs used
NtCreateTransaction() CreateFileTransacted() WriteFile() NtCreateSection() NtRollbackTransaction() NtCreateProcessEx() NtCreateThreadEx()
EarlyBird/APC Injection
- Allocates memory within a process
- Writes shellcode to the allocated memory
- Calls
QueueUserAPC()to point to the shellcode
- Shellcode executes when the process thread enters alertable state
APIs used
OpenProcess() VirtualAllocEx() WriteProcessMemory() CreateToolhelp32Snapshot() Thread32First() Thread32Next() OpenThread() QueueUserAPC()
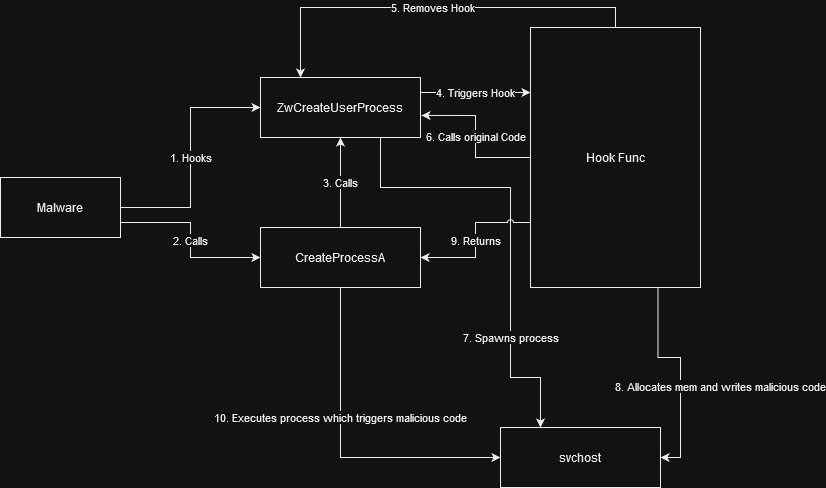
API Hooking
- Executes a target process
- Allocates region of memory inside the target process
- Writes malicious code to the allocated region
- Executes code through the target process
APIs used
CreateProcessA() ZwAllocateVirtualMemory() ZwProtectVirtualMemory() ZwWriteVirtualMemory()
Propagate Injection
- Executes a process
- Allocates region in memory in the process for shell code
- Write shell code in the allocated memory region.
- Calls
SetPropA()to modify the callback forUxSubclassInfo
- When the malware calls
SendMessageA,WM_NOTIFYandWM_PAINTis sent to the target window, which causes the shellcode to execute
APIs used
OpenProcess() VirtualAllocEx() WriteProcessMemory FindWindowEx() GetDlgItem() GetProp() ReadProcessMemory() SetProp()